Install & setup Burp Suite KaliLinux,Ubuntu
To install and set up Burp Suite on Kali Linux, follow these steps:
1. Update your system:
sqlsudo apt update
sudo apt upgrade2. Download the Burp Suite Community Edition:
bashwget https://portswigger.net/burp/releases/download?product=community&version=2021.5.3&type=Linux3. Extract the downloaded file:
tar -xvf burpsuite_community_v2021.5.3.tar.gz
4. Move the extracted folder to the desired location (e.g., /opt/):
bashsudo mv burpsuite_community/ /opt/5. Change the ownership of the Burp Suite folder
rubysudo chown -R <your_username>:<your_username> /opt/burpsuite_community/6. Create a symbolic link to easily run Burp Suite from the terminal:
bashsudo ln -s /opt/burpsuite_community/BurpSuiteCommunity /usr/bin/burpsuite7. Install Java Development Kit (JDK) if not already installed:
arduinosudo apt install default-jdk8. Configure the Java environment:
sqlsudo update-alternatives --config javaSelect the appropriate JDK version from the list and note the number associated with it.
9. Set the Java environment variable by adding the
following line to your ~/.bashrc file:
javascriptexport JDK_HOME=/usr/lib/jvm/java-{version}-openjdk-amd64Replace "{version}" with the number noted in the previous step.
10. Source the ~/.bashrc file to apply the changes:
bashsource ~/.bashrc11. Start Burp Suite:
burpsuite
When Burp Suite starts, it may prompt you to choose an installation type. Select "Temporary Project" to start with a blank project.
That's it! Burp Suite should now be installed and ready to use on your Kali Linux system. Remember to use Burp Suite responsibly and in accordance with applicable laws and regulations.
How to Protect Your WEB-APPLICATION
To protect your web application from potential security risks associated with Burp Suite or similar tools, you can implement the following measures:
1. Secure Development Practices: Follow secure coding practices when developing your web application. This includes input validation, output encoding, secure session management, and implementing strong authentication mechanisms. Adhering to security best practices reduces the likelihood of vulnerabilities that tools like Burp Suite can exploit.
2. Implement Web Application Firewalls (WAF): Deploy a WAF that can help detect and block common web application attacks. A WAF can analyze incoming requests and responses, filter out malicious traffic, and protect against common vulnerabilities, including those that Burp Suite may attempt to exploit.
3. Conduct Regular Security Testing: Perform regular security assessments of your web application using tools like Burp Suite yourself or engage professional security testers. This allows you to identify and address vulnerabilities proactively before attackers exploit them.
4. Monitor and Analyze Logs: Implement a logging mechanism in your application to capture and analyze security-related events. Monitor logs for any suspicious or abnormal activity that may indicate an attack attempt. Regularly review and analyze logs to detect potential security issues.
5. Rate Limiting and Account Lockouts: Implement rate limiting mechanisms to prevent brute-force attacks and enforce account lockouts after multiple failed login attempts. This helps protect against automated attacks and reduces the risk of unauthorized access to user accounts.
6. Implement Transport Layer Security (TLS): Use TLS to encrypt communications between the client and server. Ensure that secure cipher suites and strong encryption protocols are enabled to protect against eavesdropping and man-in-the-middle attacks. Regularly update and patch TLS implementations to address any vulnerabilities.
7. Stay Updated with Security Patches: Keep your web application and underlying frameworks up to date with the latest security patches and updates. Vulnerabilities can be discovered in various components, and timely patching helps mitigate potential risks.
8. Web Application Security Headers: Implement security headers in your web application's HTTP responses. Headers like Content-Security-Policy (CSP), X-Frame-Options, and X-XSS-Protection can provide additional layers of protection against cross-site scripting (XSS) and clickjacking attacks.
9. Access Control and Privilege Management: Implement strong access control mechanisms to ensure that users have the appropriate privileges and access levels based on their roles and responsibilities. Regularly review and update user permissions to prevent unauthorized access to sensitive data or functionality.
10. Security Awareness and Training: Educate your development team, administrators, and users about web application security best practices. Regularly provide training and awareness sessions to ensure everyone understands the potential risks, the importance of security measures, and how to use Burp Suite responsibly.
By implementing these measures, you can enhance the security of your web application and reduce the risk of exploitation by tools like Burp Suite. It's important to adopt a holistic approach to security, combining secure development practices, proactive testing, and continuous monitoring to protect your application from potential threats.



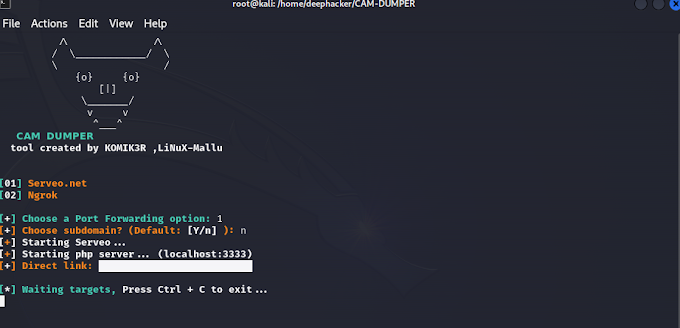



![Step-by-Step Guide: Install NetHunter Rootless on Android [2023] - No Root Required](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjr_ZkRL6AyVQsYrb3QCcsse840F2ukrgeihfWdzvaYG6DvKgRelbqvL5fC4DkxXErUxjB97vk67IzTDngE9evniR3VZt_8RXAEaCXgpHqZvuFc3eePbAh6kDSdWxjzItlt4lGdz3Dqk9W4frs-xzHocQkHjuMb45deGwPO9w2AdqNPRdkhOYG1a12_P3Q/w680/kali%20nethuter.png)
